Detect vulnerabilities before they become threats
With NESS and our Trython module, you can run vulnerability scans automatically or on-demand across your entire technology infrastructure. Our vulnerability scan process identifies security gaps early, helping you fix them before attackers can exploit them and compromise your business.
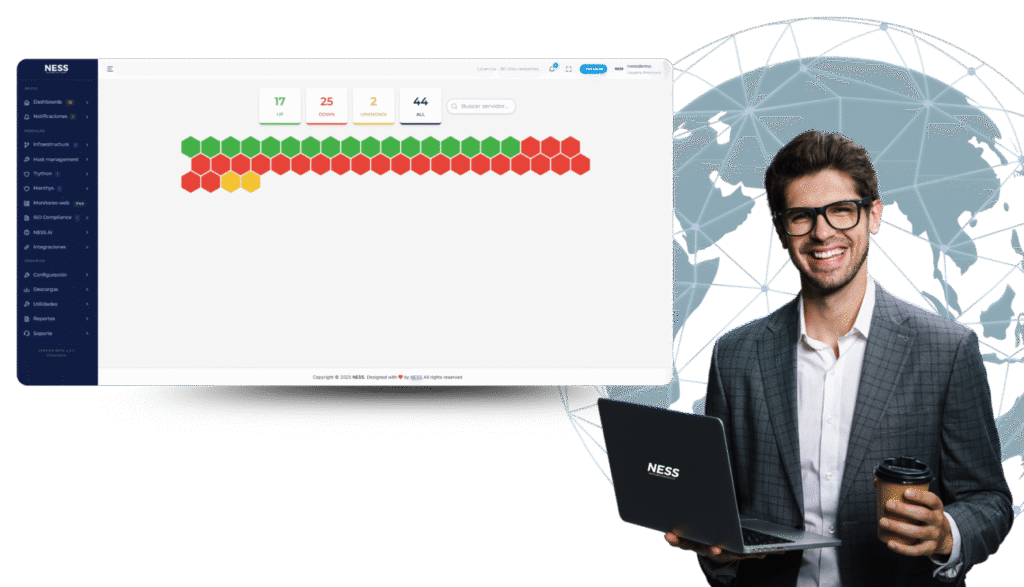
Secure your operations with continuous vulnerability scan
At NESS, we carry out continuous and automated security analysis to detect weaknesses before they are exploited. Through an intelligent vulnerability scan, our platform evaluates servers, applications, network devices, and endpoints to identify insecure configurations, outdated software, and known vulnerabilities. Each vulnerability scan allows you to address issues proactively and keep your business protected against evolving cyber threats.
How NESS vulnerability scanning works?
Our method combines advanced technology and expert analysis for accurate results.
Our experts and the NESS platform gather key information to identify your critical assets: servers, networks, web applications, databases, and connected devices.
This first vulnerability scan stage allows us to:
Map your environment and define priority services.
Detect dependencies and access points that could become attractive targets for attackers.
Through advanced continuous analysis, the platform simulates real-world attack techniques to execute a precise vulnerability scan in real time.
During this phase, we cover:
Review of insecure configurations, open ports, weak credentials, and outdated software.
Detection of known vulnerabilities (CVE), configuration errors, and poor security practices.
Scheduled and on-demand scanning adapted to infrastructure changes.
Every vulnerability scan finding is classified by criticality, potential impact, and ease of exploitation to accelerate decision-making:
Immediate alerts for critical vulnerabilities.
Clear dashboards and visual charts that show risk trends and evolution.
Smart filters by host, application, severity, or date for efficient analysis.
We don’t just show you threats — we guide you to fix them.
Each vulnerability includes:
Step-by-step technical remediation recommendations.
Integration with ticketing tools or dashboards for internal control and tracking.
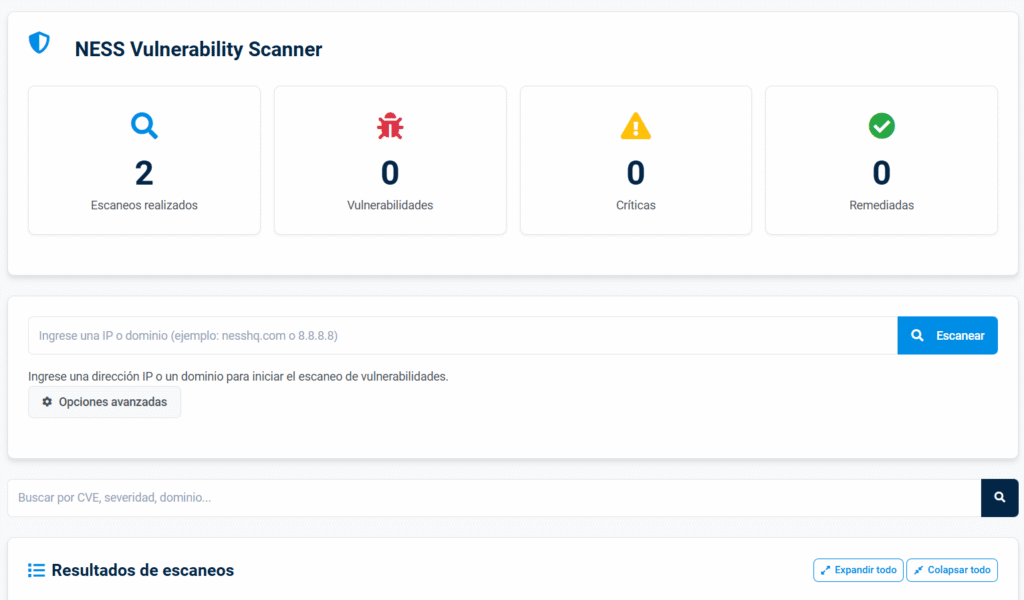
Tangible results from every vulnerability scan
Each vulnerability scan delivers clear and actionable insights to improve your cybersecurity posture:
Complete visibility of weak points across your infrastructure.
Prioritization of risks that attackers could actually exploit.
Recommended actions to strengthen security and support compliance with standards.
A reduced attack surface and greater confidence in business continuity.
Vulnerability scan: detect and block threats before they impact your business
Protect your infrastructure with cutting-edge vulnerability scan technology. Our service identifies weaknesses in servers, networks, and applications before attackers can exploit them—helping you stay one step ahead of cyber threats and ensuring continuous business protection.
How a vulnerability scan works
Protect your business today elements
Schedule a free demo or request a personalized quote to discover how our vulnerability scan solution can secure your infrastructure, reduce risks, and strengthen your cybersecurity strategy.

NESS (Network Environment Scanning and Security), focuses on developing software to help companies prevent and predict cyberattacks and failures within their technological infrastructure.


